Build your ISMS in minutes, not months.
.svg)
.svg)
.svg)
Choose frameworks, instantly get pre-filled policies and tasks, monitor compliance scores, and manage risks. All in one place.
.svg)



Vaatimukset täyttyvät jalkauttamalla digiturvatehtäviä.
Mitä kukin tekee digiturvan eteen?
Osa tehtävistä vaatii asioiden ohjeistamista henkilöstölle.
Mitä pitää muistaa arjessa?
Osa tehtävistä vaatii listausten pitoa tietoturvan ydinelementeistä.
Mistä pitää voida raportoida?































Policies in Word docs, risk lists in Excel, tasks in someone’s head without structure, nothing connects and progress is hard to track.

Trying to interpret and implement standards manually wastes time. You risk overdoing the wrong things and missing the essentials.

Even if you’re doing the right things, it’s difficult to show concrete results when your security work isn’t tied to employee awareness, real implementation outcomes or effective reporting.


Cyberday has helped hundreds of companies make the transition from unstructured information security management into a clear, compliance proving system.
Set your goals by activating the most relevant frameworks from our library. You can start from the essentials or pursue a certification level.
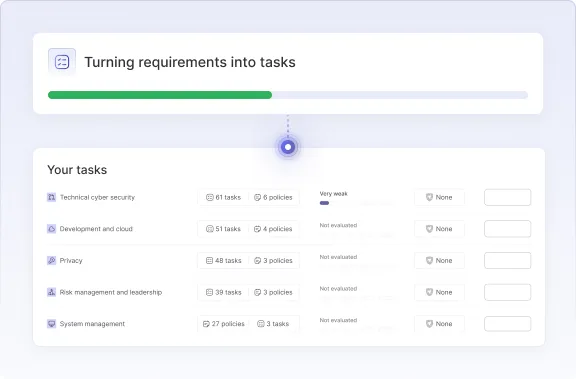
Requirements are instantly turned into concrete tasks and policies you can start implementing.
Explore Framework Library ->

Choose the first cyber security topics and start evaluating how your current measures cover requirements.
You’ll immediately see your starting compliance level, understand the gap, and know what needs to be done.
Cyberday translates complex requirements into practical, ready-made tasks. Each task connects directly to one or more frameworks and controls.
This saves you time by showing exactly what to implement.





Prove to auditors, top management or your own team that tasks are implemented with assurance information. Assurance info differs according to the task type and is automatically customized based on the task requirements.
Learn more about Assurance ->Create the desired summaries and reports of cyber security in "one click", with the report library's dynamic pre-filled templates.
Learn more about Report Automation ->
Continue advancing your clear plan, making ongoing improvements smartly:

